Before jumping to the blog let’s clarify a few technical words eg what is “CyberSecurity Incidents” as per NIST CSF definition
An occurrence that actually or imminently jeopardizes, without lawful authority, the integrity, confidentiality, or availability of information or an information system; or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or acceptable use policies. [FISMA2014]
Enough technical stuff, let’s understand in layman term what is Incident handling framework and why do we need it to update?
Imagine your home security system. It’s not just about reacting when someone breaks in, right? It’s about having good locks, knowing your neighborhood risks, training your family, detecting suspicious activity, responding quickly if something happens, and learning from any incidents to make your home even safer.
In the cybersecurity world, dealing with attacks (which we call incidents) is similar. We need a plan – a lifecycle – to handle these situations effectively. The National Institute of Standards and Technology (NIST) has updated its Cybersecurity Framework (CSF) to version 2.0, and this includes a fresh way of looking at the incident response lifecycle.
In the past, cybersecurity incidents were rare, small-scale, and could be resolved quickly—usually within a day or two. Incident response was treated as a separate process done by a dedicated team, with improvements made after the incident and fed into a cycle of preparation. Responses were occasional rather than ongoing.
Nowadays, incidents happen often, are more damaging, and take weeks or months to resolve due to their complexity and dynamic nature. Incident response is now a key part of managing cybersecurity risks and needs to be integrated across an organization’s operations. Lessons from incidents should be shared immediately instead of waiting until recovery is over. Continuous improvement is essential to tackle modern threats effectively.
Let’s break it down in simple terms and see how it’s better than the old way.
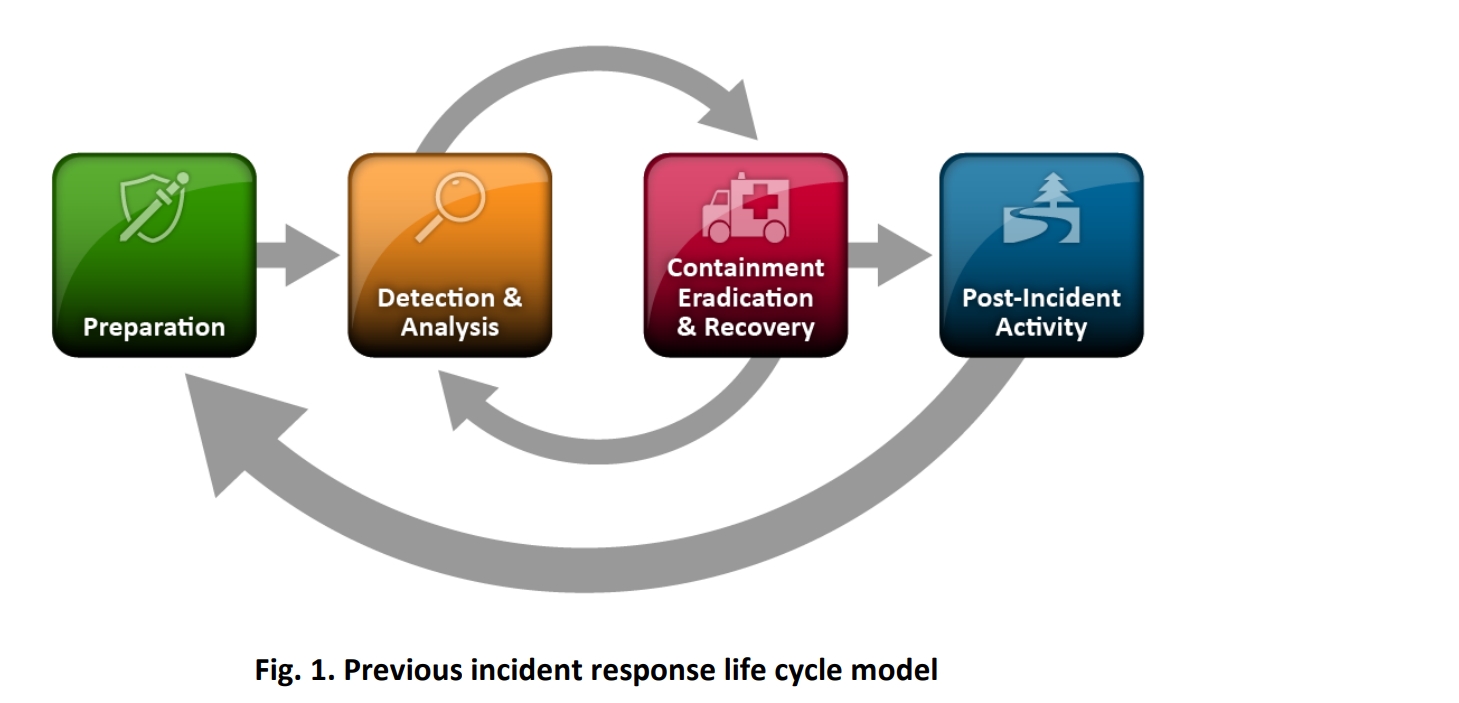
The Old School: A Four-Step Reaction
 Source: NIST
Source: NIST
Older incident response in a more linear, four-step process:
1.Preparation: Getting ready with plans, tools, and training.
2.Detection & Analysis: Figuring out if something bad is happening and what it is.
3.Containment, Eradication & Recovery: Stopping the problem from spreading, getting rid of it, and bringing things back to normal.
4.Post-Incident Activity: Learning from what happened to prevent future issues.
Think of it like putting out a fire: get the extinguishers ready, see the smoke and find the fire, put it out and fix the damage, then figure out how the fire started so it doesn’t happen again.
This model worked okay when incidents were less frequent and less complex. But the cyber landscape has changed dramatically. Attacks are now common, more damaging, and can take weeks or even months to fully recover from. This older model sometimes felt too isolated from the bigger picture of overall security.
The New Era: Incident Response Integrated with Your Whole Security Strategy (NIST CSF 2.0)
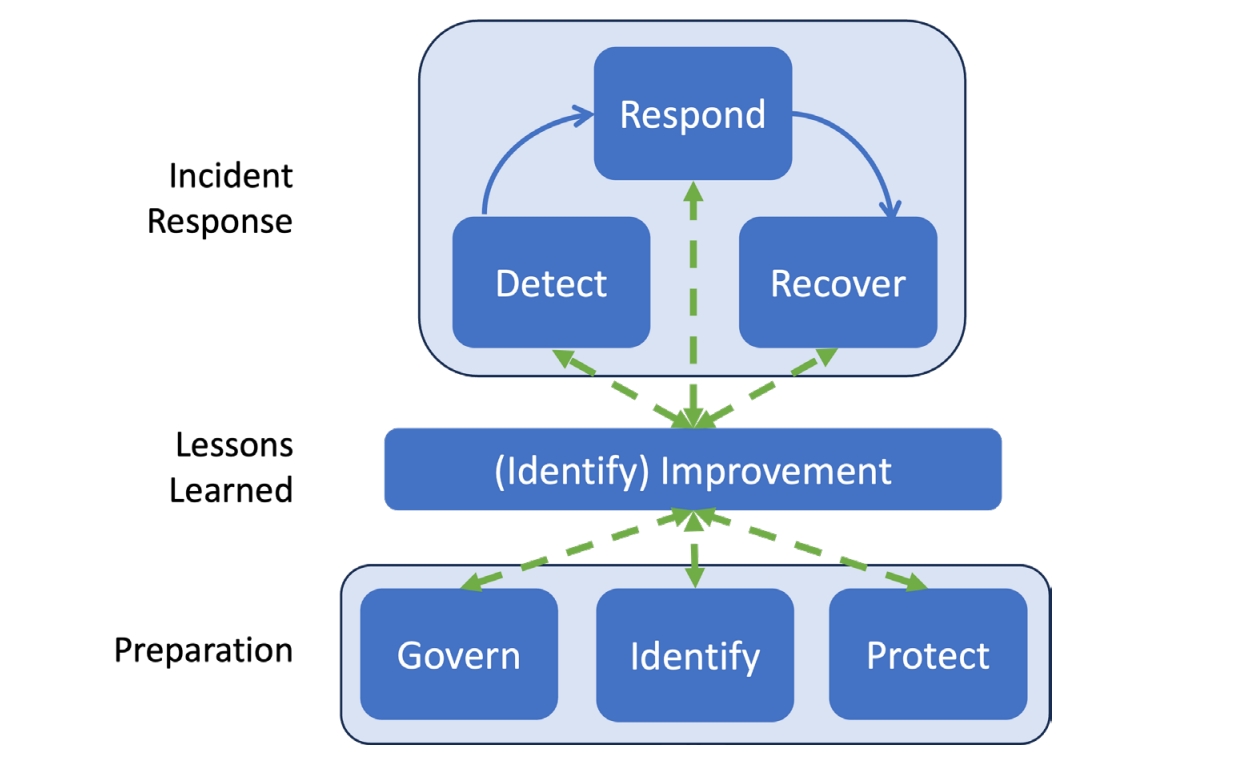
NIST CSF 2.0 takes a more comprehensive approach, weaving incident response into the fabric of your entire cybersecurity risk management strategy. It uses six core functions to organize how we think about cybersecurity:
 source : NIST
source : NIST
-
Govern (GV): This is like setting the rules and making sure everyone understands the security strategy, expectations, and policies. It’s the leadership and oversight part.
-
Identify (ID): Knowing what you have (your digital assets) and understanding the cybersecurity risks you face is crucial
-
Protect (PR): Putting safeguards in place to manage those risks and prevent incidents from happening in the first place
-
Detect (DE): Continuously looking for signs of attacks and potential problems
-
Respond (RS): Taking action when an incident is detected. This includes managing, prioritizing, containing, and getting rid of the threat, as well as communicating about it
-
Recover (RC): Restoring your systems and operations after an incident
With CSF 2.0, the incident response lifecycle isn’t just steps you take after an attack. It’s influenced and supported by all six of these functions
• Govern, Identify, and Protect are like your preventative measures: They help you avoid some incidents, prepare for the ones that do happen, and limit their impact. For instance, knowing your critical assets (Identify) and having strong access controls (Protect) makes it harder for attackers to succeed. Having clear policies (Govern) ensures everyone knows their role in security and incident response.
- Detect, Respond, and Recover are the actions you take when an incident occurs. But even these are improved by the other functions. For example, knowing your normal network activity (Identify, Continuous Monitoring in Detect) helps you spot unusual behavior more easily.
Side-by-Side: Comparing the Old and New
| Older Incident Response Phase | Corresponding CSF 2.0 Functions |
|---|---|
| Preparation | Govern, Identify (all Categories), Protect |
| Detection & Analysis | Detect, Identify (Improvement Category) |
| Containment, Eradication & Recovery | Respond, Recover, Identify (Improvement Category) |
| Post-Incident Activity | Identify (Improvement Category) |
As you can see, the new model isn’t just about replacing steps; it’s about embedding incident response thinking throughout your entire cybersecurity posture.
Visualise
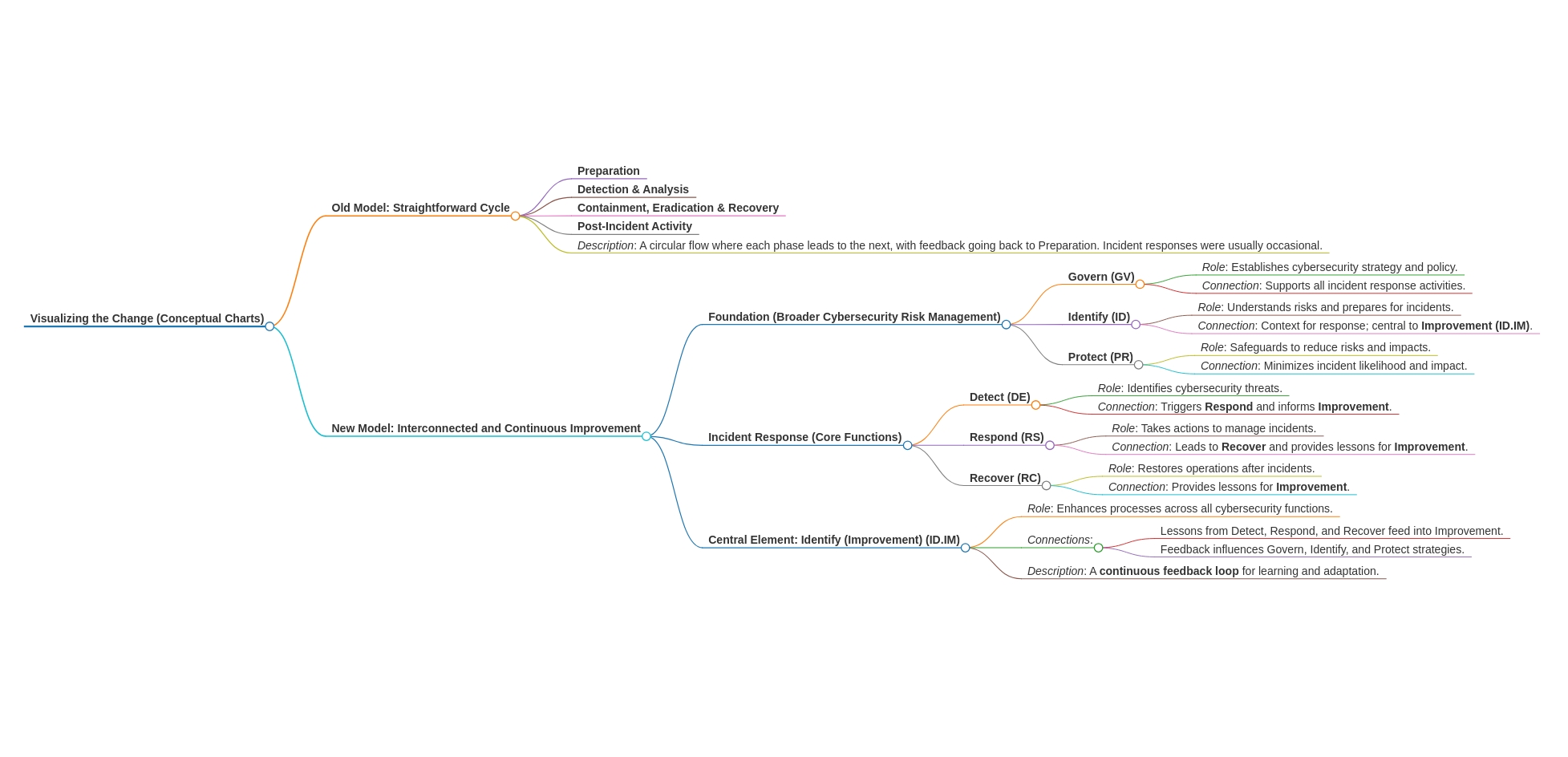
The new model is less of a separate “break-the-glass” process and more of an ongoing, integrated part of how you manage cyber risk.

